You don’t have to be great to start, but you have to start to be great.
Zig Ziglar
I may not be an expert in all things cloud-based, but I challenged myself to learn as much as possible because I enjoy exploring various fields of cybersecurity. So, for my first home lab project, I created a live security operations centre (SOC) mini honeynet in Microsoft Azure.
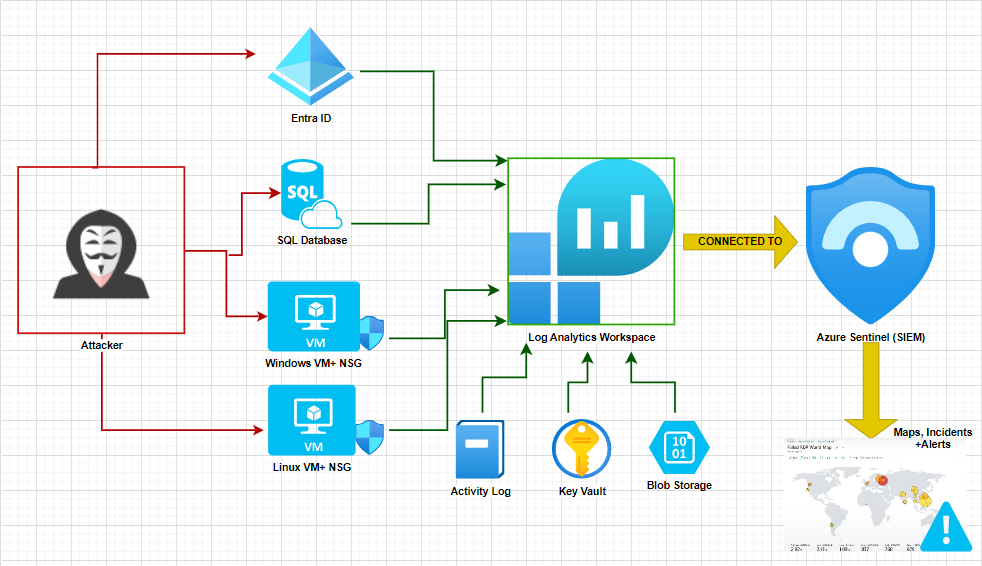
The goal of the project was to run an insecure environment for 24 hours, implement security measures, and then run the environment for another 24 hours to collect and compare security data. I used a Log Analytics workspace as my log aggregator to gather all the data. Then, I utilised Microsoft Sentinel to analyse the logs, which helped me generate attack maps, set off alerts, and create incidents.
Creating a honeynet in Azure
I started this project by creating a free subscription Azure account (Tenant) and proceeded to create three virtual machines (VMs):
- Windows VM (with SQL server downloaded onto it.)
- Windows VM (that I used to attack my other two VMs)
- Linux VM.
After setting up my virtual machines, I configured the Network Security Group (NSG) to allow all inbound traffic. An NSG is a virtual layer 4 firewall that manages inbound and outbound traffic to and from virtual machines within a network according to user-defined rules. I then opened all the built-in VM firewalls, except for the attack VM, and deployed resources, such as key vault and blob storage, with public endpoints visible to the internet. After several hours, I noticed unauthorised attempts to log in from unknown sources.

Running an Insecure Environment for 24 hours
When I finished creating my virtual machines and resources, I set up a Log Analytics Workspace. I then enabled log collection for various components such as VMs, Network Security Groups, Entra ID logs, Azure Activity Logs, Key Vault, and storage account. When this was done, I configured Sentinel and connected it to my Log Analytics Workspace. I enabled Microsoft Defender for Cloud in the Environment Settings, including Log Analytics Workspace, Subscriptions, and Continuous Export. Afterwards, I simulated various attack scenarios to generate logs and practised querying them using Kusto Query Language (KQL). Finally, I left the VMs running for 24 hours to gather security metrics from live traffic.
After 24 hours these were the results I collected:
| Metric | Count |
| Start time | 09/04/24 18:20 |
| Stop time | 10/04/24 18:20 |
| SecurityEvent (Windows VM | 36 875 |
| Syslog (Linux VM) | 2 286 |
| SecurityAlert (Microsoft Defender for Cloud) | 9 |
| SecurityIncident (Sentinel) | 311 |
| NSG inbound malicious flow allowed | 2 123 |
Using the data collected, I created attack maps using map queries in Sentinel to show where the traffic was coming from.



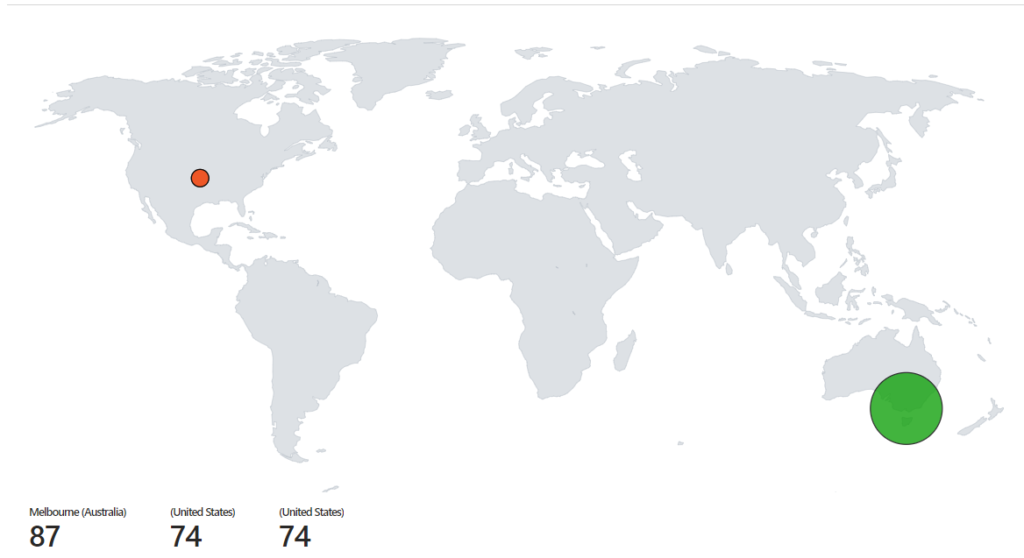
Running a Secure environment for 24 hours
Once I collected the necessary data for the insecure environment, I proceeded to improve its security by implementing the National Institute of Standards and Technology (NIST) 800-53 framework. I blocked all incoming traffic except for my admin computer on the NSG. Also, I ensured that all other resources were protected with their own firewalls (FW) and private endpoints (PE).

After 24 hours these were the results I collected:
| Metric | Count |
| Start time | 11/04/24 18:16 |
| Stop time | 12/04/24 18:16 |
| SecurityEvent (Windows VM) | 14 399 |
| Syslog (Linux VM) | 3 |
| SecurityAlert (Microsoft Defender for Cloud) | 0 |
| SecurityIncident (Sentinel) | 0 |
| NSG inbound malicious flow allowed | 0 |
I could not create any maps because no malicious activity was detected within the 24-hour period after the hardening process.
Conclusion
Building a mini honeynet in Azure was a challenging but rewarding endeavour. Through this project, I learned a lot about the Azure environment and the various services it offers. I also realised the importance of hardening digital environments because attackers are always looking for vulnerabilities, no matter how small they may be. The experience has renewed my confidence, and I have already begun applying the skills I learned to my day job. I am excited to start my next project to see what else I can learn.
Leave a Reply